Recently Updated
Rabbit Hole
Challenge
Here’s a picture of my favorite vegetable. I hope it doesn’t make you cry.

Solution
After a lot of experimenting, we find out we can uncover a hidden message from the image using steghide:
1
2
3
$ steghide extract -sf rabbithole.jpg
Enter passphrase: <onion>
wrote extracted data to "address.txt".
whoo! contents of the file address.txt is:
1
wsqxiyhn23zdi6ia
might be an .onion link? Opening http://wsqxiyhn23zdi6ia.onion with a tor browser (or via https://onion.link/) gives:

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
<!DOCTYPE HTML>
<html>
<head>
<title>Rabbit Hole</title>
<meta charset="UTF-8">
<style>
body {
background: black;
}
p {
max-width: 750px;
text-align: center;
color: #00ff00;
margin: 0px auto;
}
#header {
max-width: 989px;
margin: 0px auto;
}
#footer {
margin: 100px 0;
text-align: center;
}
#error {
max-width: 350px;
}
#eyes {
max-width: 200px;
}
</style>
</head>
<body>
<div id="header">
<img id="error" src="error.gif"/>
</div>
<p>聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ𓅡𔕨𓁯𓅤 [..] </p>
<div id="footer">
<img id="eyes" src="eyes.gif"/>
</div>
</body>
</html>


We find nothing in the images, but after some hints we find that the chinese characters are base65536
1
2
3
4
5
6
7
8
9
# pip install base65536
import base65536
with open('rabbithole_characters.txt','r') as f:
ct = f.readline().rstrip().replace(' ','')
with open('rabbithole_out','wb') as f2:
f2.write(base65536.decode(ct))
which turns out to be an epub on cell phone hacking. Searching the contents for the flag gives it to us
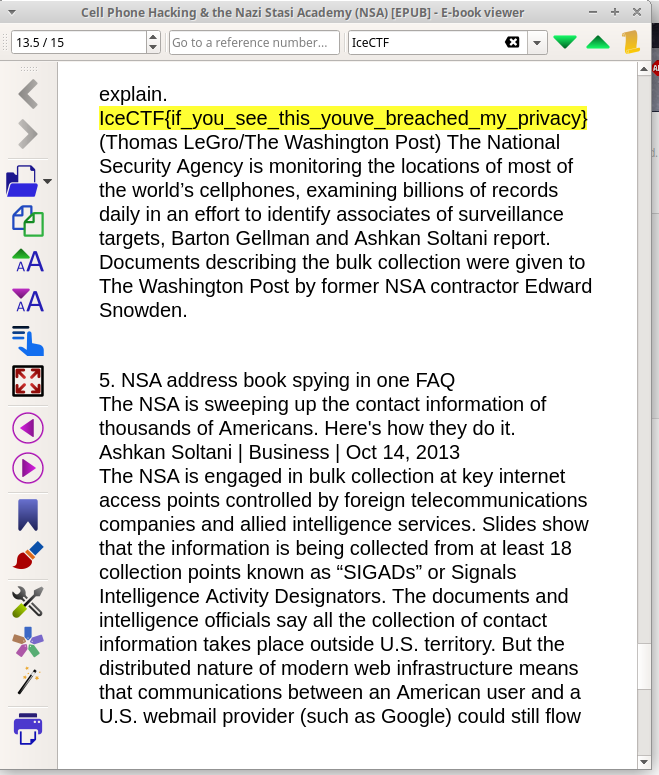
Flag
1
IceCTF{if_you_see_this_youve_breached_my_privacy}
Flag
IceCTF{if_you_see_this_youve_breached_my_privacy} 