Overview
| Challenge | Difficulty | Points | Category | Flag |
|---|---|---|---|---|
| Prison Break | easy | he18-gx8L-AJUw-DSMH-6aUI | ||
| Babylon | easy | he18-egu6-pL6f-QjmF-qXWj | ||
| Pony Coder | easy | he18-lSvO-A4tC-AdzR-3iFk | ||
| Memeory | easy | he18-cGoS-a2tz-BD2w-zXH8 | ||
| Slopppy and Paste | easy | he18-2yTc-bJ1f-raIQ-gKc6 | ||
| Cooking for Hackers | easy | he18-MdVx-nSgb-wzYT-TtoE | ||
| Jigsaw | easy | he18-jFsP-AXNB-GUXu-dkms | ||
| Disco Egg | easy | he18-Qox7-xFIw-cljk-ySdF | ||
| Dial Trial | easy | he18-Yuk0-9zPD-l8Di-aL1i | ||
| Level Two | medium | unsolved | ||
| De Egg you must | medium | unsolved | ||
| Patience | medium | unsolved | ||
| Sagittarius | medium | unsolved | ||
| Same Same | medium | he18-D76U-PvxZ-7Icy-mkF1 | ||
| Manile Greetings | medium | he18-ifiI-T6ZT-TNyX-9DZp | ||
| Git Cloak | medium | he18-k4oU-OEar-n9Sr-ULi0 | ||
| Space Invaders | medium | he18-D76U-PvxZ-7Icy-mkF | ||
| Egg Factory | medium | unsolved | ||
| Virtual Hen | hard | unsolved | ||
| Artist No Name Yet | hard | unsolved | ||
| Hot Dog | hard | unsolved | ||
| Block Jane | hard | unsolved | ||
| Rapbid Learning | hard | unsolved | ||
| ELF | hard | unsolved |
Prison Break
Challenge
Your fellow inmate secretly passed you an old cell phone and a weird origami. The only thing on the phone are two stored numbers.
1
2
555-7747663 Link
555-7475464 Sara
Find the password and enter it in the Egg-o-Matic below. lowercase only, no spaces!

Solution
Combine the telephone numbers with the dots on the origami and a T9 pad:

1
2
3
4
5
6
7
8
7747663 (Link)
1334322 (number of dots)
prisone (1 times '7' key = p, 3 times '7' key = r, 3 times '4' key = i, etc)
7475464 (Sara)
3342321 (number of dots)
risking
this reads prisonerisking, enter this into egg-o-matic to get our egg

Flag
he18-gx8L-AJUw-DSMH-6aUI Babylon
Challenge
s not the only thing in Babylon which has walls and shelves.
1
4 - 4 - 28 - 355
Solution
This refers to the Library of Babel, from a short story written by Jorge Luis Borges. The library in the story contains every single possible 410 page book. Most will be jibberish, but it will also contain every 410 page book ever written or that ever will be written.
This concept has been made into a on online version: https://libraryofbabel.info/
We can find the book, on hexagon given by the content of the text file, wall 4, shelf 4, volume 28, page 355.
This leads to a page which is mostly spaces an the following sentence:
1
the super secret hackyeaster password is checkthedatayo
we enter this into the egg-o-matic to get our egg

Flag
he18-egu6-pL6f-QjmF-qXWj Pony Coder
Challenge
Tony the pony has encoded something for you. Decode his message and enter it in the egg-o-matic below! Lowercase and spaces only, and special characters!
1
gn tn-gha87be4e
Solution
Pony Coder refers to Punycode
we can prepend xn-- and use an online conversion tool such as this one to translate xn--gn tn-gha87be4e to gìn tônì©
this doesn’t work when we put it in the the egg-o-matic, but we try gin tonic and that does work

Flag
he18-lSvO-A4tC-AdzR-3iFk Memeory
Challenge
Fancy a round of memeory?
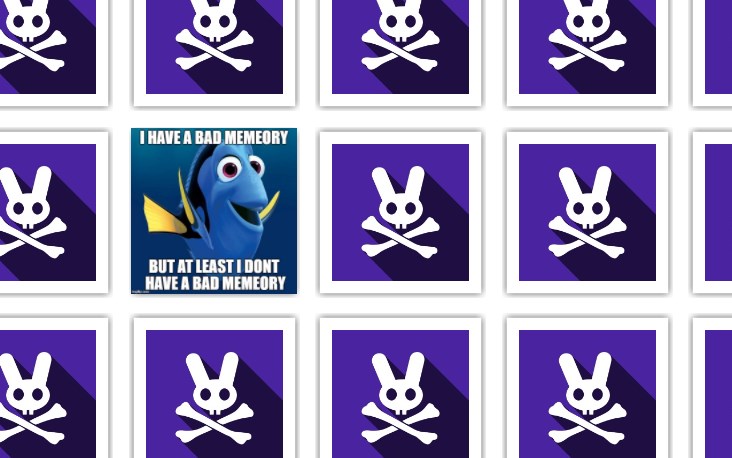
Click here to play.
Solution
nspect the html, and can see the images on each of the cards:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
<div class="moduleLegespiel">
<figure id="legespiel_card_63" class="">
<a href="#card_63">
<img class="boxFront" src="./lib/32.jpg">
<img class="boxWhite" src="./lib/shadow_card.png">
<img class="boxBack" src="./lib/back.jpg">
</a>
<img class="boxStretch" src="./lib/shim.gif">
</figure><figure id="legespiel_card_58" class="">
<a href="#card_58">
<img class="boxFront" src="./lib/30.jpg">
<img class="boxWhite" src="./lib/shadow_card.png">
<img class="boxBack" src="./lib/back.jpg">
</a>
<img class="boxStretch" src="./lib/shim.gif">
</figure><figure id="legespiel_card_84">
<a href="#card_84">
<img class="boxFront" src="./lib/43.jpg">
<img class="boxWhite" src="./lib/shadow_card.png">
<img class="boxBack" src="./lib/back.jpg">
</a>
<img class="boxStretch" src="./lib/shim.gif">
</figure><figure id="legespiel_card_73">
<a href="#card_73">
<img class="boxFront" src="./lib/37.jpg">
<img class="boxWhite" src="./lib/shadow_card.png">
<img class="boxBack" src="./lib/back.jpg">
</a>
<img class="boxStretch" src="./lib/shim.gif">
</figure><figure id="legespiel_card_19">
[..]
so we just find the pairs and play the game to get our egg:


Flag
he18-cGoS-a2tz-BD2w-zXH8 Slopppy and Paste
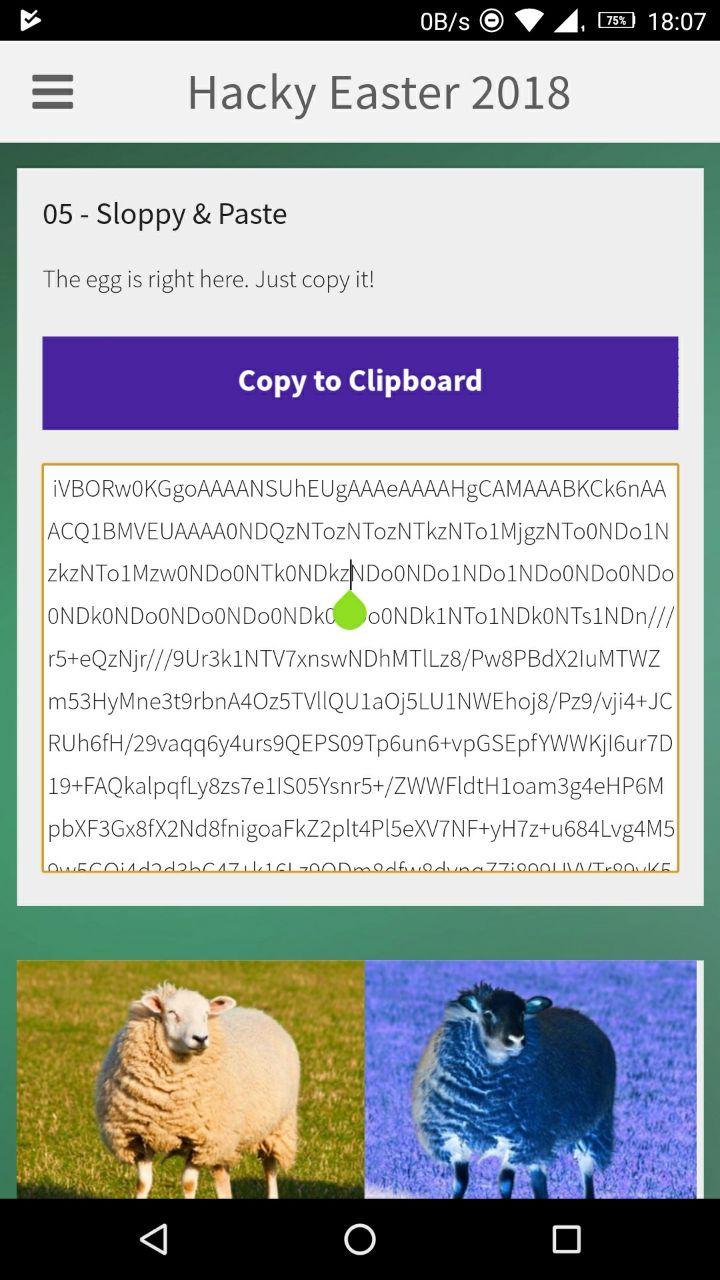
Challenge
This was a mobille challenge.
Solution
When we try to copy the text shown, it copies a different text
so we get the apk of the mobile app and decode it
1
apktool decode HackyEaster_9_5.0.1.apk
and find the string we are looking for in assets/www/challenge05.html

Flag
he18-2yTc-bJ1f-raIQ-gKc6 Cooking for Hackers
Challenge
1
2
3
4
5
6
7
8
9
10
11
12
13
You've found this recipe online:
1 pinch: c2FsdA==
2 tablesspoons: b2ls
1 teaspoon: dDd3Mmc=
50g: bnRkby4=
2 medium, chopped: b25pb24=
But you need one more secret ingredient! Find it!
Solution
These b64 decode to
1
2
3
4
5
6
7
1 pinch: salt
2 tablesspoons: oil
1 teaspoon: t7w2g
50g: ntdo.
2 medium, chopped: onion
But you need one more secret ingredient! Find it!
The period at the end of the fourth part is the hint, this is a url!
1
saltoilt7w2gntdo.onion
open it with a tor browser to get the egg

Flag
he18-MdVx-nSgb-wzYT-TtoE Jigsaw
Challenge
Thumper was probably under time pressure and jumped around a bit too wild. As a result, his picture has broken.
Can you write a program to put it back together

Solution
This tool is pure magic and solved this challenge for us using a genetic algorithm: https://github.com/nemanja-m/gaps
1
$ gaps --image=../jigsaw.png --generations=30 --population=600 --save

1
goodsheepdontalwayswearwhite
We put this phrase into the egg-o-matic to get our egg

Flag
he18-jFsP-AXNB-GUXu-dkms Disco Egg
Challenge
1
2
3
Make things as simple as possible but no simpler.
-- Albert Einstein
Solution
We are led to a site with an egg continually chaning colour

The element of the disco egg look as follows in the source:
1
2
3
4
5
6
7
8
<div id="overlay">
<table><tr>
<td class="cyan black green darkgreen blue orange red darkgrey brown" style="background-color:#006412;"></td>
<td class="cyan red brown blue black green darkgrey" style="background-color:#FBF305;"></td>
<td class="cyan black blue red lightgrey" style="background-color:#FBF305;"></td>
<td class="darkgreen black tan cyan green blue" style="background-color:#FBF305;"></td>
<td class="brown blue darkgrey cyan mediumgrey lightgrey black darkgreen" style="background-color:#FF6403;"></td>
[..]
we notice that each element has either black or white in the list but not both. We let the background color reflect this and find our QR code
1
2
3
4
5
cat disco.html
| sed 's|</td>|</td>\n|g'
| sed 's|class=\".*white.*|class=\"white\" style=\"background-color:#FFFFFF;\"></td>|g'
| sed 's|class=\".*black.*|class=\"black\" style=\"background-color:#000000;\"></td>|g'
> disco2.html

Flag
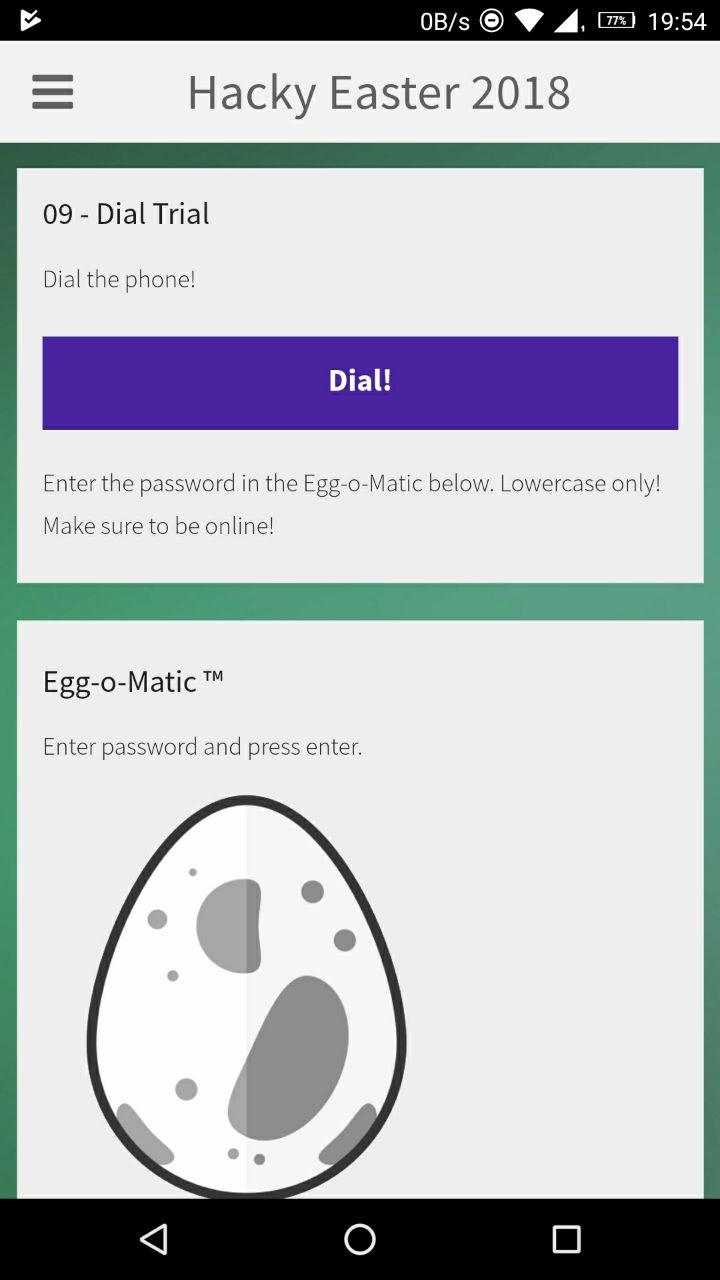
he18-Qox7-xFIw-cljk-ySdF Dial Trial
Challenge
Another mobile challenge 
Solution
we find the mp3 file played by the app when hitting the button.
We convert it to wav file and decode the DTMF tones using http://dialabc.com/sound/detect/index.html
1
472612252336262636253412
This looks like it could be similar to the first challenge, each pair of number representing a letter, 47 means 4 times number 7 (letter s in T9)
1
2
47 26 12 25 23 36 26 26 36 25 34 12
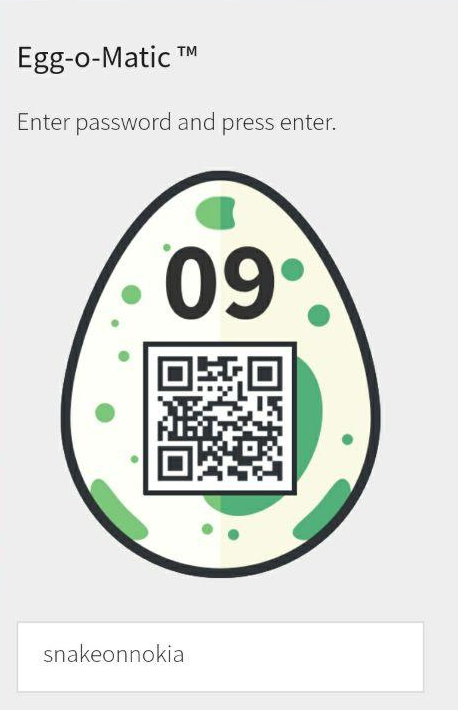
s n a k e o n n o k i a
Whoo! we enter snakeonnokia in the egg-o-matic to get our egg
Flag
he18-Yuk0-9zPD-l8Di-aL1i Level Two
Challenge
So you managed to beat the boss in the teaser game? This one won’t be that easy!
You’ll need RPG Maker Run Time Packages to run the game.
Hints: There are several parts to be found. Combine them, and enter the final flag in the egg-o-matic below, without spaces! Saving the game from time to time certainly helps.
Solution
Flag
unsolved De Egg you must
Challenge
Who was first, the cat or the egg?

Solution
The zip file is password protected but easily cracked with fcrackzip and this wordllist
1
2
3
4
5
6
7
8
9
10
11
$ fcrackzip -v --use-unzip -D -p dictionaries/password basket.zip
found file 'egg1', (size cp/uc 1389653/1433600, flags 9, chk 4f21)
found file 'egg2', (size cp/uc 1426168/1433600, flags 9, chk 4f21)
found file 'egg3', (size cp/uc 1425557/1433600, flags 9, chk 4f21)
found file 'egg4', (size cp/uc 1425787/1433600, flags 9, chk 4f21)
found file 'egg5', (size cp/uc 1423266/1433600, flags 9, chk 4f21)
found file 'egg6', (size cp/uc 362705/384584, flags 9, chk 4f21)
PASSWORD FOUND!!!!: pw == thumper
1
2
3
$ file egg1
egg1: ISO Media, Apple iTunes Video (.M4V) Video
The first file looks like a video, but it doesn’t play properly. We try to extract frames and get the following error:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ ffmpeg -i egg1.m4v -r 1/1 $filename%03d.jpg
ffmpeg version 3.3.4-2 Copyright (c) 2000-2017 the FFmpeg developers
built with gcc 7 (Ubuntu 7.2.0-8ubuntu2)
configuration: --prefix=/usr --extra-version=2 --toolchain=hardened --libdir=/usr/lib/x86_64-linux-gnu --incdir=/usr/include/x86_64-linux-gnu --enable-gpl --disable-stripping --enable-avresample --enable-avisynth --enable-gnutls --enable-ladspa --enable-libass --enable-libbluray --enable-libbs2b --enable-libcaca --enable-libcdio --enable-libflite --enable-libfontconfig --enable-libfreetype --enable-libfribidi --enable-libgme --enable-libgsm --enable-libmp3lame --enable-libopenjpeg --enable-libopenmpt --enable-libopus --enable-libpulse --enable-librubberband --enable-libshine --enable-libsnappy --enable-libsoxr --enable-libspeex --enable-libssh --enable-libtheora --enable-libtwolame --enable-libvorbis --enable-libvpx --enable-libwavpack --enable-libwebp --enable-libx265 --enable-libxvid --enable-libzmq --enable-libzvbi --enable-omx --enable-openal --enable-opengl --enable-sdl2 --enable-libdc1394 --enable-libiec61883 --enable-chromaprint --enable-frei0r --enable-libopencv --enable-libx264 --enable-shared
libavutil 55. 58.100 / 55. 58.100
libavcodec 57. 89.100 / 57. 89.100
libavformat 57. 71.100 / 57. 71.100
libavdevice 57. 6.100 / 57. 6.100
libavfilter 6. 82.100 / 6. 82.100
libavresample 3. 5. 0 / 3. 5. 0
libswscale 4. 6.100 / 4. 6.100
libswresample 2. 7.100 / 2. 7.100
libpostproc 54. 5.100 / 54. 5.100
[mov,mp4,m4a,3gp,3g2,mj2 @ 0x55e2047e2f20] moov atom not found
egg1: Invalid data found when processing input
a moov atom contains metadata about the video link.
We remember the challenge description cat or the egg so we concatenate the different files together to get a working video
1
$ cat egg* > eggall
We notice some marking at the bottom of the frames during the last second orso, but not sure what that means?
1
$ ffmpeg -i eggall -y -ss 24 -an -r 20 frame%03d.jpg
Flag
unsolved Patience
Challenge
Solution
Flag
unsolved Sagittarius
Challenge
13 - Sagittarius…
… is playing with his pila again.
Can you find the Easter egg QR code he has hidden from you?
Solution
I loaded pila.kmz into a KMZ viewer and saw this:

So obviously the wrong projection.
Flag
unsolved Same Same
Challenge
Same same… …but different! Upload the right files and make the server return an Easter egg!
1
http://whale.hacking-lab.com:4444
Solution
We get some PHP code:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
<?php
require __DIR__ . "/vendor/autoload.php"; // QR decoder library from https://github.com/khanamiryan/php-qrcode-detector-decoder
try {
$qrcode1 = new QrReader($_FILES["file1"]["tmp_name"]);
$answer1 = $qrcode1->text();
} catch(Exception $e) {
exit("Error while reading the first QR.");
}
try {
$qrcode2 = new QrReader($_FILES["file2"]["tmp_name"]);
$answer2 = $qrcode2->text();
} catch(Exception $e) {
exit("Error while reading the second QR.");
}
if(($answer1 == "Hackvent" && $answer2 == "Hacky Easter" or $answer1 == "Hacky Easter" && $answer2 == "Hackvent") && sha1_file($_FILES["file1"]["tmp_name"]) == sha1_file($_FILES["file2"]["tmp_name"])) {
[SURPRISE]
}
else {
echo ":-(";
}
?>
The PHP code seems to require that we upload two files which are QR codes with the word ‘Hackvent’ in one and ‘Hacky Easter’ in the other, and that those files should have identical sha1sums.
I just assumed it would accept PDFs without looking since the sha1 collision for pdfs was pretty recently big news. Found https://github.com/nneonneo/sha1collider as one of the top results in a search.
1
2
3
4
5
$ qrencode 'Hackvent' -o a.png
$ qrencode 'Hacky Easter' -o b.png
$ convert a.png a.pdf
$ convert b.png b.pdf
$ python3 sha1collider/collide.py a.pdf b.pdf --progressive
and got out two PDFs with identical hashes in under a second! Neat.
1
2
bdece875ca36c6505b0728cbeca7495db1a30246 out-a.pdf
bdece875ca36c6505b0728cbeca7495db1a30246 out-b.pdf

Flag
he18-D76U-PvxZ-7Icy-mkF1 Manile Greetings
Challenge
Randy Waterhouse receives a package from his friend Enoch Root containing a deck of cards and a letter:
Dear Randy,
even though our stay in Manila was not very pleasant, I fondly think of our discussions there:
1
GTIFL RVLEJ TAVEY ULDJO KCCOK P
Wishing you happy Easter
Enoch
Solution
The text is a hint to the book Cryptonomicon by Neal Stephenson. Combined with the cards image, we realize this is a Solitaire Cipter
if we convert the notation of the deck slightly we can solve it online here
key:
1
8d 3s 7d 3d 2c 5s Ad 6c 7s 6d A Kd Qh Js Jc 7h 3h 9h 9s 8s 9c As 4h 8c 3c Kh Ah 6s 6h Ts Ks Ac Td Qd Qc B Qs 4s 9d 2s 5c Jh Th 4c Tc 5d 8h 2h 2d Jd 7c Kc 5h 4d
which gives output:
1
THEPA SSWOR DISCR YPTON OMICO N
So the password is CRYPTONOMICON, and we put that into the egg-o-matic to get our flag

Flag
he18-ifiI-T6ZT-TNyX-9DZp Git Cloak
Challenge
This one requires your best Git-Fu! Find the hidden egg in the repository.
Solution
The zip files contains a git repo with a number of images in it:
Flag
he18-k4oU-OEar-n9Sr-ULi0 Space Invaders
Challenge
Alien space invaders left a secret message. Luckily, you know that they used codemoji.org for the encryption.
Decrypt the message, and save the planet!!
⚾⭐📯💵🎨📢📘💪☀🌆💪🐸🎨🐦📢
Solution
- Go to https://codemoji.org/#/encrypt
- create a random message
“share”, they give you a shortlink that resolves into “https://codemoji.org/share.html?data=….” where data is an html encoded, base64 encoded blob of json like:
1 2 3 4
{ "message": "⚾⭐📯💵🎨📢📘💪☀🌆💪🐸🎨🐦📢", "key": "👾" }
- replace the message with the given input: “⚾⭐📯💵🎨📢📘💪☀🌆💪🐸🎨🐦📢”
- and get this url
- which decodes with the invader emoji to
invad3rsmustd13

Flag
he18-D76U-PvxZ-7Icy-mkF Egg Factory
Challenge
Make the egg factory write a secret word!
Then enter it into the Egg-o-Matic below, uppercase and underscores only.
Solution
Flag
unsolved Virtual Hen
Challenge
Virtual hen lays virtual eggs. But only with the correct password it is an Easter Egg!
Solution
Flag
unsolved Artist No Name Yet
Challenge
Great musical compositions are being published lately, by an unknown producer. Nobody was able yet to unveil the genius behind. It is said that he or she is placing secret messgages in his compositions.
You got hold of the original files of the latest masterpiece. Uncover the hidden message, and enter it into the Egg-o-Matic below, case and digits only.
Solution
Flag
unsolved Hot Dog
Challenge
or: how to solve this darn crypto challenge to get your sleep back.
Enter the flag found, into the Egg-o-Matic below, without brackets.
Solution
Flag
unsolved Block Jane
Challenge
You intercepted an encryped message by Jane. Can you decrypt it?
You know that AES was used, and that the following service is receiving such encrypted messages:
1
whale.hacking-lab.com 5555
Find the password and enter it in the Egg-o-Matic below!
Solution
Flag
unsolved Rapbid Learning
Challenge
The SERTC (super exciting rabbit travel company) wants to use the latest technology.
They currently employ an experienced guide, which is classifying the visitors into Goodtails and Luckyspoons. For the trained eye of the guide, this is easy. But how do you get a machine to do it (which would be cheaper)?
Go and help them implement a learning algorithm! Their platform is available here:
http://whale.hacking-lab.com:2222
Since quality is the main concern of SERTC, they expect an accuracy of at least 99%.
Solution
Flag
unsolved ELF
Challenge
The Egg Liberation Front (ELF) already marked this binary. Go ahead and free the egg!
Once the right PIN is provided, the binary spills out the Easter egg QR code.
Solution
Flag
unsolved 








 The egg with the QR code translates to `7dUDQDhMQkLYsQTMJq62`, but this is not a valid egg of course. ```bash $ git log commit b9e860f47fe6990cbda4ac5bb3d2829d2191f1eb (HEAD -> master) Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:16 2018 -0500 even more funny images added commit 3839c14d2863fd850794661677352305ea798eb6 Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:15 2018 -0500 more funny images added commit 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:15 2018 -0500 created the funny git meme repo ``` We rewind the commits to see if there is anything interesting ```bash $ git reset HEAD~2 Unstaged changes after reset: M 02.png D 04.png ``` we see that image 2 was modified and another image deleted   but alas, this different egg (QRcode reads `qdUX0sgDVjWxiFNifHKE`) is still not what we are looking for.. ```bash $ git log --all --graph --oneline * b9e860f (HEAD -> master) even more funny images added | * 9a29769 (branch) branch created |/ * 3839c14 more funny images added * 228b603 created the funny git meme repo ``` So we see that a different branch was created at some point, but we don't find the egg here either. ```bash $ cat .git/config [core] repositoryformatversion = 0 filemode = false bare = false logallrefupdates = true symlinks = false ignorecase = true [user] name = PS email = ps@hacking-lab.com ``` ```bash $ cat .git/logs/HEAD [29-03-18 13:00:39] 0000000000000000000000000000000000000000 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 commit (initial): created the funny git meme repo 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from master to temp 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed b9820d55ce59799992648672a5a43fff4effd56b PS <ps@hacking-lab.com> 1516704195 -0500 commit: temp branch created b9820d55ce59799992648672a5a43fff4effd56b 9d7c9b5a1c8773ea48caac90d05401679b0a8897 PS <ps@hacking-lab.com> 1516704195 -0500 commit: added one more image 9d7c9b5a1c8773ea48caac90d05401679b0a8897 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from temp to master 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704195 -0500 commit: more funny images added 3839c14d2863fd850794661677352305ea798eb6 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from master to branch 3839c14d2863fd850794661677352305ea798eb6 9a29769663d029f1b3ad83fec7e7f19ca1cf8e78 PS <ps@hacking-lab.com> 1516704195 -0500 commit: branch created 9a29769663d029f1b3ad83fec7e7f19ca1cf8e78 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704196 -0500 checkout: moving from branch to master 3839c14d2863fd850794661677352305ea798eb6 b9e860f47fe6990cbda4ac5bb3d2829d2191f1eb PS <ps@hacking-lab.com> 1516704196 -0500 commit: even more funny images added $ git log --all --branches --remotes --tags --reflog --oneline --graph * b9e860f (HEAD -> master) even more funny images added | * 9a29769 (branch) branch created |/ * 3839c14 more funny images added | * 9d7c9b5 added one more image | * b9820d5 temp branch created |/ * 228b603 created the funny git meme repo ``` ``` git checkout 9d7c9b5a1c8773ea48caac90d05401679b0a8897 ``` gives us another image, `tree.jpg` and yet another version of `02.png`:   Eventually discovered `git fsck` notes a dangling blob which is apparently some piece of data that was included at one point but the commit was later removed or backed out. ```console $ git fsck Prüfe Objekt-Verzeichnisse: 100% (256/256), Fertig. dangling blob dbab6618f6dc00a18b4195fb1bec5353c51b256f $ git cat-file -p dbab6618f6dc00a18b4195fb1bec5353c51b256f > tmp.png $ file tmp.png tmp: PNG image data, 480 x 480, 8-bit colormap, non-interlaced ``` 
The egg with the QR code translates to `7dUDQDhMQkLYsQTMJq62`, but this is not a valid egg of course. ```bash $ git log commit b9e860f47fe6990cbda4ac5bb3d2829d2191f1eb (HEAD -> master) Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:16 2018 -0500 even more funny images added commit 3839c14d2863fd850794661677352305ea798eb6 Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:15 2018 -0500 more funny images added commit 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed Author: PS <ps@hacking-lab.com> Date: Tue Jan 23 05:43:15 2018 -0500 created the funny git meme repo ``` We rewind the commits to see if there is anything interesting ```bash $ git reset HEAD~2 Unstaged changes after reset: M 02.png D 04.png ``` we see that image 2 was modified and another image deleted   but alas, this different egg (QRcode reads `qdUX0sgDVjWxiFNifHKE`) is still not what we are looking for.. ```bash $ git log --all --graph --oneline * b9e860f (HEAD -> master) even more funny images added | * 9a29769 (branch) branch created |/ * 3839c14 more funny images added * 228b603 created the funny git meme repo ``` So we see that a different branch was created at some point, but we don't find the egg here either. ```bash $ cat .git/config [core] repositoryformatversion = 0 filemode = false bare = false logallrefupdates = true symlinks = false ignorecase = true [user] name = PS email = ps@hacking-lab.com ``` ```bash $ cat .git/logs/HEAD [29-03-18 13:00:39] 0000000000000000000000000000000000000000 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 commit (initial): created the funny git meme repo 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from master to temp 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed b9820d55ce59799992648672a5a43fff4effd56b PS <ps@hacking-lab.com> 1516704195 -0500 commit: temp branch created b9820d55ce59799992648672a5a43fff4effd56b 9d7c9b5a1c8773ea48caac90d05401679b0a8897 PS <ps@hacking-lab.com> 1516704195 -0500 commit: added one more image 9d7c9b5a1c8773ea48caac90d05401679b0a8897 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from temp to master 228b603ed45ddaf1b1d3fe502e168fa2508ee5ed 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704195 -0500 commit: more funny images added 3839c14d2863fd850794661677352305ea798eb6 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704195 -0500 checkout: moving from master to branch 3839c14d2863fd850794661677352305ea798eb6 9a29769663d029f1b3ad83fec7e7f19ca1cf8e78 PS <ps@hacking-lab.com> 1516704195 -0500 commit: branch created 9a29769663d029f1b3ad83fec7e7f19ca1cf8e78 3839c14d2863fd850794661677352305ea798eb6 PS <ps@hacking-lab.com> 1516704196 -0500 checkout: moving from branch to master 3839c14d2863fd850794661677352305ea798eb6 b9e860f47fe6990cbda4ac5bb3d2829d2191f1eb PS <ps@hacking-lab.com> 1516704196 -0500 commit: even more funny images added $ git log --all --branches --remotes --tags --reflog --oneline --graph * b9e860f (HEAD -> master) even more funny images added | * 9a29769 (branch) branch created |/ * 3839c14 more funny images added | * 9d7c9b5 added one more image | * b9820d5 temp branch created |/ * 228b603 created the funny git meme repo ``` ``` git checkout 9d7c9b5a1c8773ea48caac90d05401679b0a8897 ``` gives us another image, `tree.jpg` and yet another version of `02.png`:   Eventually discovered `git fsck` notes a dangling blob which is apparently some piece of data that was included at one point but the commit was later removed or backed out. ```console $ git fsck Prüfe Objekt-Verzeichnisse: 100% (256/256), Fertig. dangling blob dbab6618f6dc00a18b4195fb1bec5353c51b256f $ git cat-file -p dbab6618f6dc00a18b4195fb1bec5353c51b256f > tmp.png $ file tmp.png tmp: PNG image data, 480 x 480, 8-bit colormap, non-interlaced ``` 