Egg 18: Sharks on a Wire
Challenge:
In this challenge, you need to get access to a web site.
Inspect the following capture files, in order to get the credentials needed.
Solution:
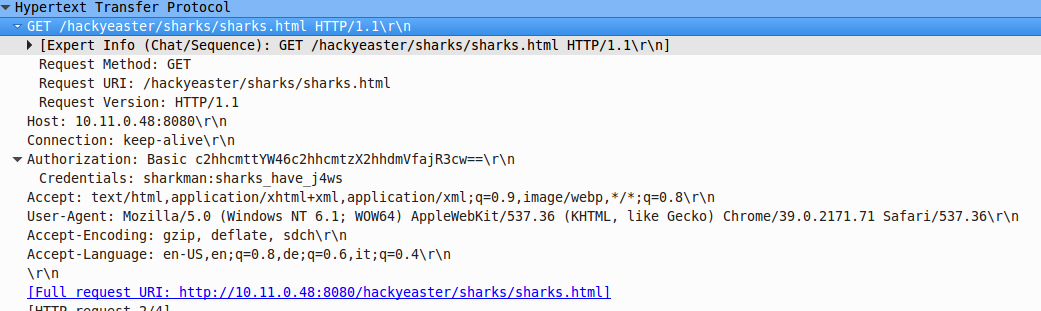
The website requires HTTP authentication
in wireshark we can find the auth credentials
1
sharkman:sharks_have_j4ws
we enter these and get to a website where we have to fill in another set of credentials

but we can find these in the pcap file as well:
1
user=supershark&pass=hashed%21%21%21&hash=b3f3ca462d3fa58b74d6982af14d8841b074994a
HTML source for the page:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
<!DOCTYPE HTML>
<html>
<head>
<title>Sharks on Wire</title>
<meta http-equiv="content-type" content="text/html; charset=utf-8" />
<link rel="icon" type="image/ico" href="../images/favicon.ico">
<link rel="stylesheet" type="text/css" href="sharks.css">
<script src="../js/jquery.min.js"></script>
<script type="text/javascript" src="../js/crypto-js/sha1.js"></script>
<script type="text/javascript" src="../js/crypto-js/core-min.js"></script>
<script type="text/javascript" src="../js/crypto-js/enc-base64-min.js"></script>
<body>
<div class="title">Sharks on Wire</div>
<div class="panel">
<form action="auth" method="post" onsubmit="$('#hash').val(CryptoJS.SHA1($('#pass').val()));$('#pass').val('hashed!!!');">
<input class="input" type="text" name="user" placeholder="User"/>
<input class="input" type="password" name="pass" id="pass" placeholder="Password"/>
<input class="input" type="hidden" name="hash" id="hash" />
<input class="button" type="submit" value="Dive in"/>
</form>
</div>
</body>
</html>
we do not know the password, but we do know the hash and see that the hash is calculated client-side, so we do not need to know the password.
In the HTML we change the hash input type from hidden to text and enter the value b3f3ca462d3fa58b74d6982af14d8841b074994a,

we also change the onsubmit action to $('#hash').val($('#hash').val());$('#pass').val('hashed!!!'); so that we do not calculate the hash from the password but use it directly.
This leads us to the egg:

Flag
83OHadUPAeWRfd6YBv6t 